Spectre, Meltdown and VMware vSphere
Many people are under the incorrect belief that it is hardware-level firmware updates from companies like HPE and Dell that will protect our Virtual Machines from Speculative Execution Vulnerabilities. This is NOT TRUE.
- As far as your VMs are concerned, the VM BIOS and Hypervisor are the hardware!
When VMware gets around to re-releasing vSphere updates that address Speculative Execution Vulnerabilities (CVE-2017-5753 aka ‘Spectre Variant 1’, CVE-2017-5715 aka ‘Spectre Variant 2’, CVE-2017-5754 aka ‘Meltdown Variant 3’), I have every expectation that all of your VMs will be protected from Speculative Execution Vulnerabilities that occur within the Guest OS
Server hardware firmware and BIOS updates that have been released and will be released in coming days will address Speculative Execution Vulnerabilities of the Hypervisor itself, and other VMkernel processes, which generally ONLY occur within our Management Networks.
This is one more great reason to isolate your VMware vSphere Management networks and harden them from general access, limiting use to named users and network locations! If a potential malicious actor cannot access a vulnerable element (as, perhaps, the vSphere Embedded Host Client interface) they cannot exploit Speculative Execution Vulnerabilities.
This is not to say that server hardware and firmware should not be updated as soon as updates are available, but merely to encapsulate risk where it belongs:
| Infrastructure Item: | Vulnerable area: |
| Guest OS | All clients of Guest |
| Bios | Potentially all clients of Guest |
| Hypervisor (ESXi) | All clients of Guest |
| Server Hardware | Entire Management Network, but not Guest OS |
Specific actions you should take:
- Patching your VMs with the latest available updates from the OS Vendor/Distro is the first and most effective step you can take to protect your Environment at this time.
- Use InSpectre.exe to scan/protect Windows systems. You can download InSpectre.exe from Gibson Research Corporation (its creator) here: https://www.grc.com/inspectre.htm
- Use spectre-meltdown-checker.sh to scan your Linux VMs. spectre-meltdown-checker.sh is available at: https://raw.githubusercontent.com/speed47/spectre-meltdown-checker/master/spectre-meltdown-checker.sh
- Use InSpectre.exe to scan/protect Windows systems. You can download InSpectre.exe from Gibson Research Corporation (its creator) here: https://www.grc.com/inspectre.htm
- Updating your Virtual Machine Version to the latest version will update the BIOS and help protect your Guest OS
- Using the Web Client, go to: VM > Edit Settings > Upgrade > Schedule VM Compatibility Upgrade – this may require a reboot of your VMs!
- Using Update Manager, remediate to the pre-defined baseline for: VM Hardware Upgrade to Match Host (Predefined) – this may require a reboot of your VMs!
- Updating your ESXi Hypervisor (when code is available and tested) should be all that is required to protect your Guest OSs (VMs) against all three Variants.
- We will keep you posted as patches become available and meet our abridged testing/waiting period of one week from release (for Speculative Execution Vulnerabilities only)
- Applying firmware updates to your server hardware (as it becomes available) protects your hypervisor and all processes that run directly against the hardware (VMkernel). This is most important for protection against internal vulnerabilities, but will likely do little to protect your VMs from Speculative Execution Vulnerabilities executed within the VM, as those Vulnerabilities will be mitigated by the items covered in 1-3
- Monitor your server vendor website for firmware updates
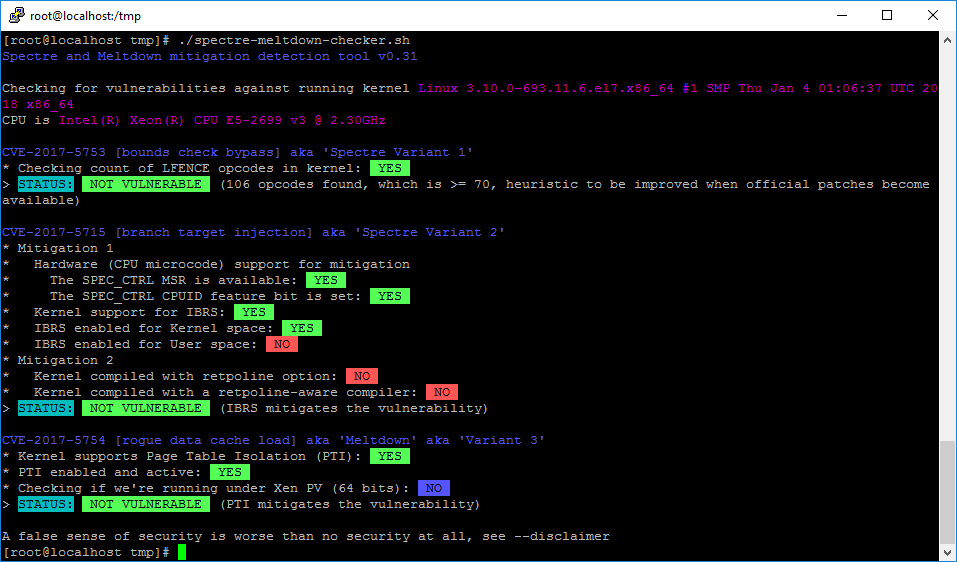
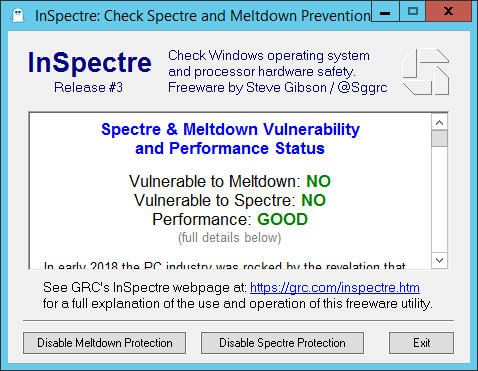
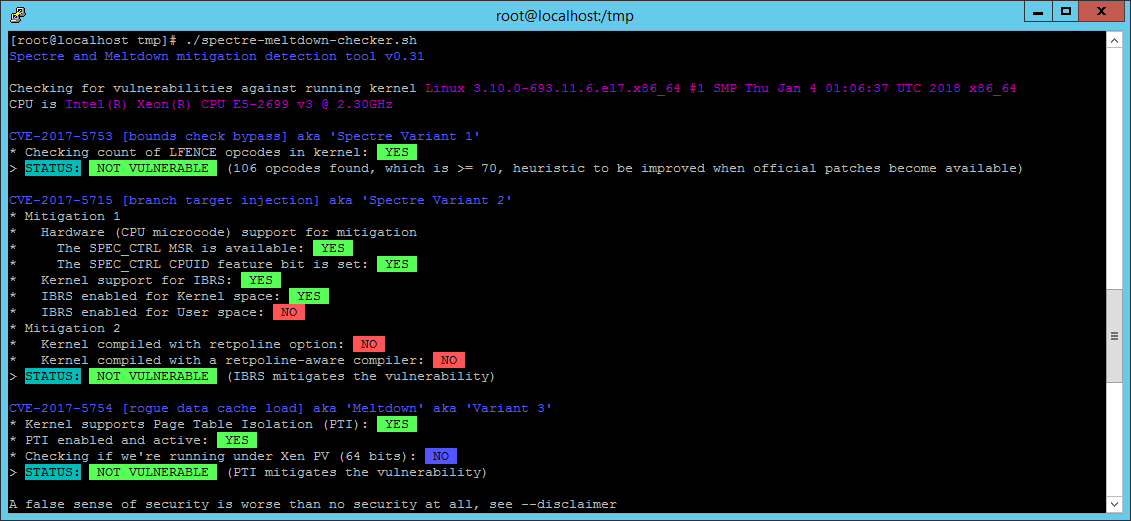
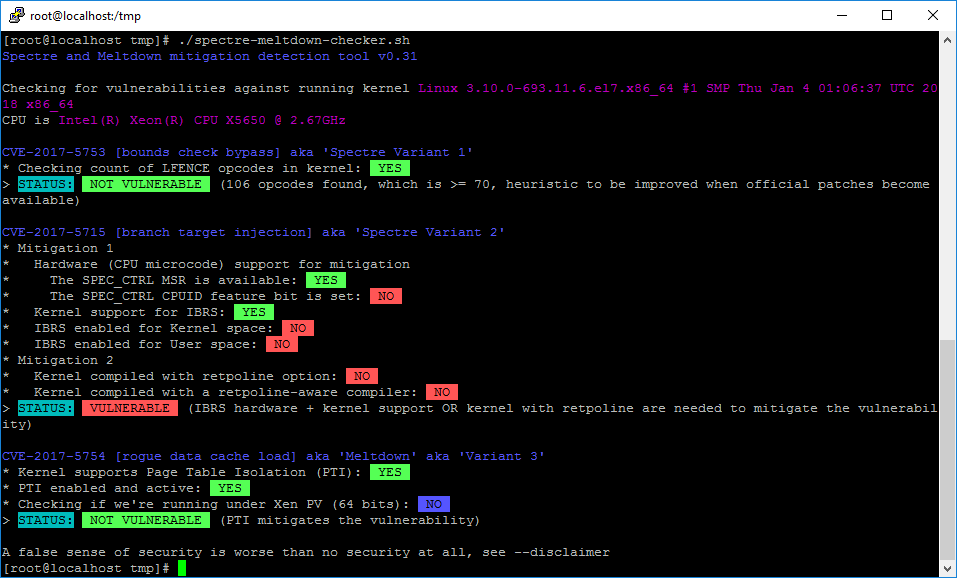
Speculative Execution Vulnerabilities Test Result Summary
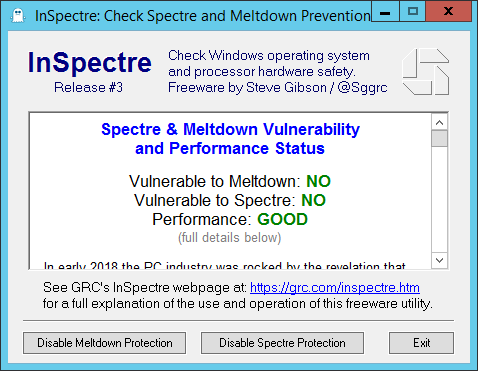
InSpectre.exe Result from a full-updated Windows Server 2012
- VM Hardware Version 11
- ESXi Host with no Hypervisor updates specific to Speculative Execution Vulnerabilities
- No Firmware updates specific to Speculative Execution Vulnerabilities
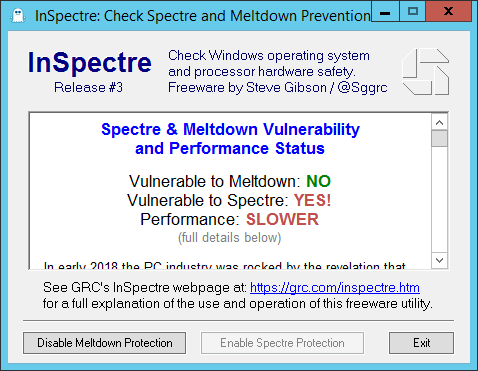
InSpectre.exe Result from a full-updated Windows Server 2012
- VM Hardware Version 11
- ESXi Host patched with the now-withdrawn 1/9/2018 updates specific to Speculative Execution Vulnerabilities
- I DO NOT recommend applying the withdrawn updates, even if you have them downloaded. See: https://kb.vmware.com/s/article/52345
- If you applied the withdrawn updates see: https://kb.vmware.com/s/article/52345
- No Firmware updates specific to Speculative Execution Vulnerabilities
InSpectre.exe Result from a full-updated CentOS7 x64
- VM Hardware Version 11
- ESXi Host with no Hypervisor updates specific to Speculative Execution Vulnerabilities
- No Firmware updates specific to Speculative Execution Vulnerabilities
InSpectre.exe Result from a full-updated CentOS7 x64
- VM Hardware Version 11
- ESXi Host patched with the now-withdrawn 1/9/2018 updates specific to Speculative Execution Vulnerabilities
- I DO NOT recommend applying the withdrawn updates, even if you have them downloaded. See: https://kb.vmware.com/s/article/52345
- If you applied the withdrawn updates see: https://kb.vmware.com/s/article/52345
- No Firmware updates specific to Speculative Execution Vulnerabilities